Last week GitHub released another new feature: GPG signature verification.
While it may seem something new, Git already supports signing commits and tags with GPG . Still, GitHub turned easier to verify if the commit is signed by the author, introducing a badge next to the commit UUID.
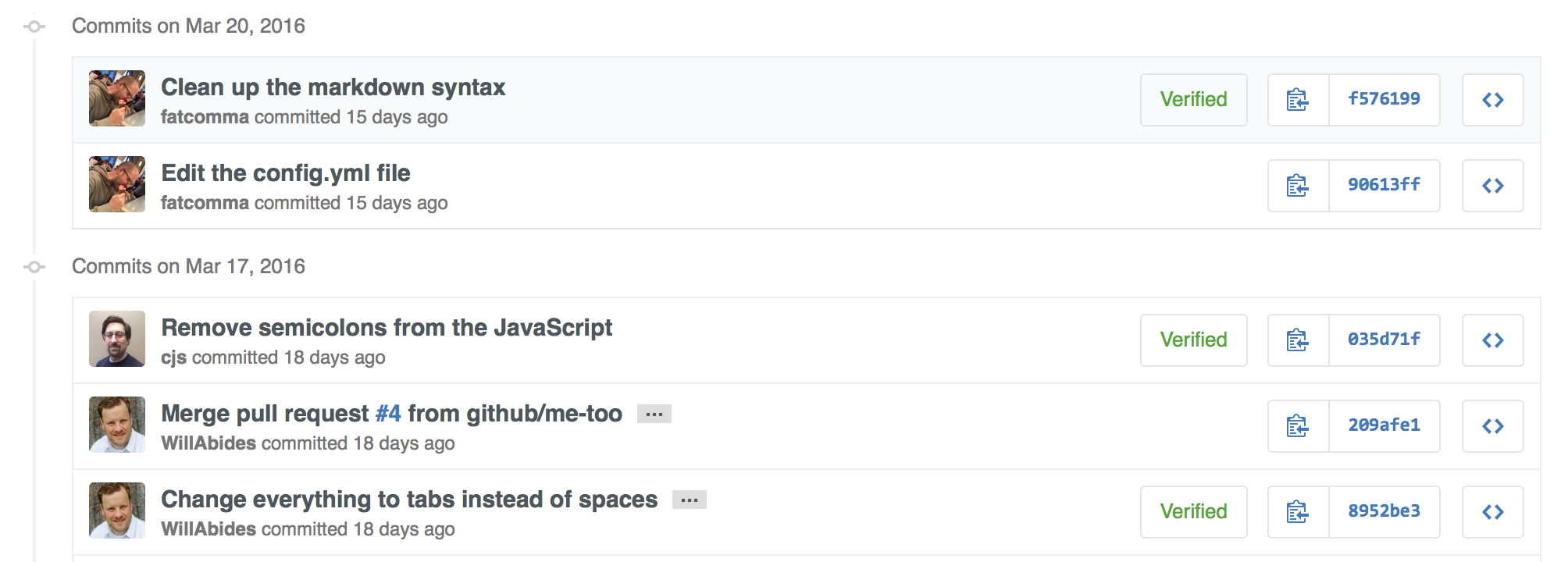
How to sign my own commits
If you want GitHub to display your verified commits there are a couple of steps required. GitHub provides a very good explanation on that.
- Assuming you don’t have a GPG key yet, you need to generate a new one.
- Now that you have a GPG key, add it to GitHub.
- Configure git to use your key
- Start signing your commits. It may be useful to define some git aliases to automate commit signature.
- Push to your GitHub repository and see the verification badge.
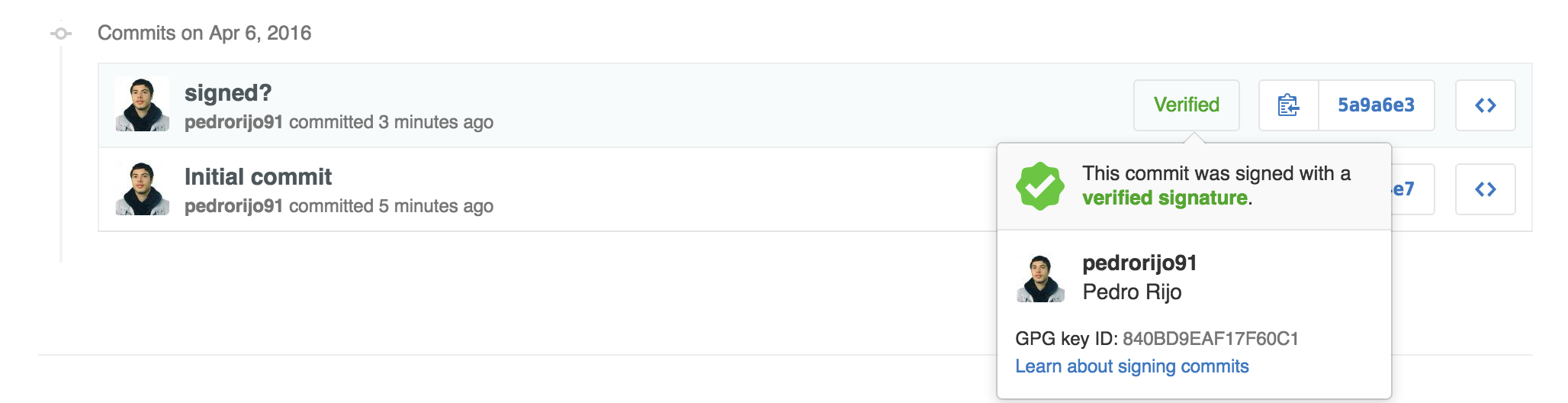
What about now?
Signing your commits is nice, but what for? Well, signing your work provides a guarantee that you did the work. But how can I verify that?
Starting by git itself, the git log command contains a flag to show signatures
$ git log --show-signatures
commit 5a9a6e3c5089ead02ce4ae4ee5f600626edf04b5
gpg: Signature made Wed Apr 6 00:22:16 2016 WEST using RSA key ID F17F60C1
gpg: Good signature from "Pedro Rijo (pedrorijo91) <some-email@mail.com>"
Author: pedrorijo91 <some-email@mail.com>
Date: Wed Apr 6 00:22:16 2016 +0100
<message>
commit 5c644e7fee2d09dbc177f515c3936ff3e787373c
Author: Pedro Rijo <some-email@mail.com>
Date: Wed Apr 6 00:20:06 2016 +0100
<message>
Git can be told to inspect and reject when merging a commit that does not carry a trusted GPG signature with the --verify-signatures command:
$ git merge --verify-signatures <non-verified-branch>
fatal: Commit ab06180 does not have a GPG signature.
$ git merge --verify-signatures <verified-branch>
Commit 13ad65e has a good GPG signature by Scott Chacon (Git signing key) <schacon@gmail.com>
Updating 5c3386c..13ad65e
Fast-forward
README | 2 ++
1 file changed, 2 insertions(+)
Unfortunately it seems that GitHub doesn’t offer pull-request/commits protection with signature verification yet, so you would have to do it manually.
In the meanwhile, have fun pranking your collegues who still doesn’t sign their commits, faking commits to look as they did it.
More about GPG
One question that will probably cross your mind, is how to distribute your public key, so that others can verify your commit signature. I googled a bit and I found other people with the same question. I found pgp.mit.edu nice and I used it myself to distribute my public key. Another popular option seems to be Keybase.io, but I haven’t tested yet.
